Introduction to UFW
UFW is a firewall configuration tool that runs on top of iptables and is included by default within Ubuntu distributions. It provides a streamlined interface for configuring common firewall use cases via the command line1. If you’re new to UFW, it simplifies the process of setting up and managing your firewall rules. Whether you want to allow or block services by port, network interface, or source IP address, UFW makes it easier to secure your system.
Table of Contents
Installation and Basic Configuration
Install UFW (if not already installed):
UFW is pre-installed on most Ubuntu systems. If not, you can install it with:
sudo apt install ufwCheck UFW Status and Rules:
Verify that UFW is active:
sudo ufw statusBy default, UFW denies incoming traffic and allows outgoing traffic.
Set Default Policies:
Define default policies to minimize attack vectors:
sudo ufw default allow outgoing
sudo ufw default deny incoming
Allow Specific Connections:
For example, to allow SSH connections:
sudo ufw allow OpenSSH Or ufw allow ssh
Deny Connections:
To deny a specific port (e.g., HTTP):
sudo ufw deny 80 you can do ufw deny 80/tcp or only udp - ufw deny 80/udp
List Rules:
View existing rules:
sudo ufw status numbered to see numbrer of the rule to use for delete 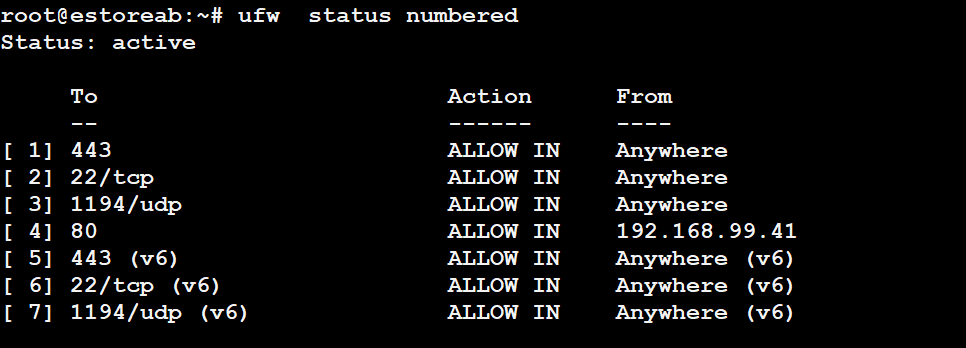
Delete Rules:
Remove a rule by its number:
sudo ufw delete RULE_NUMBER after evry delete nubmber list will change so pleae call the command again Disable UFW (if needed):
Temporarily disable UFW:
sudo ufw disableReset Rules (if necessary):
Reset UFW to default settings:
sudo ufw resetCreating Custom Rules
Allow Specific Ports:
To allow incoming traffic on a specific port (e.g., port 8080):
sudo ufw allow 8080Allow Specific IP Addresses:
To allow connections from a specific IP address (e.g., 192.168.1.100):
sudo ufw allow from 192.168.1.100Allow Specific IP Addresses in the port 443 :
To allow connections from a specific IP address (e.g., 192.168.1.100):
sudo ufw allow from 192.168.1.100 to any port 443Allow Specific Subnets:
To allow connections from an entire subnet (e.g., 192.168.1.0/24):
sudo ufw allow from 192.168.1.0/24Allow Specific Protocols:
To allow a specific protocol (e.g., UDP):
sudo ufw allow proto udp
Allow Specific Port Ranges:
To allow a range of ports (e.g., ports 6000 to 6010):
sudo ufw allow 6000:6010/tcp
Deny Specific Connections:
To deny a specific port (e.g., port 443):
sudo ufw deny 443Logging and Monitoring
Enable UFW Logging:
First, verify if UFW logging is enabled:
sudo ufw status verbose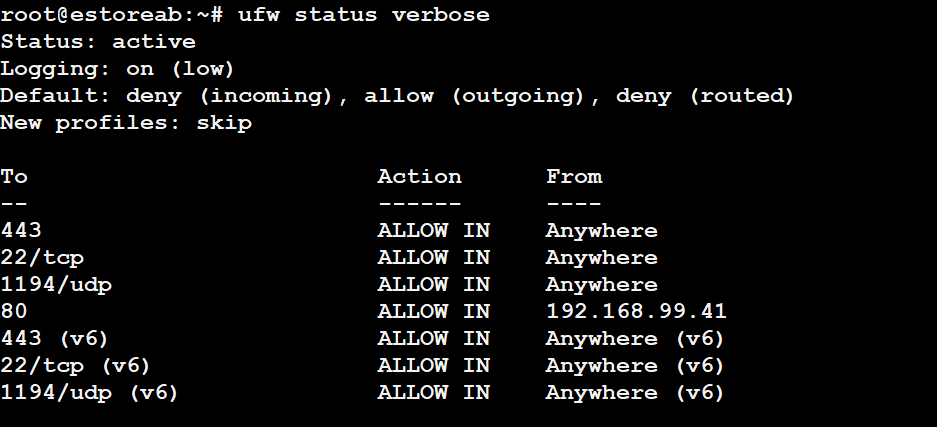
If it shows “Logging: on (low),” you’re good to go. Otherwise, enable it with:
sudo ufw logging onView UFW Logs:
To check UFW firewall logs, use the less command:
sudo less /var/log/ufw.log
Monitoring Live Logs:
For real-time monitoring, use the tail command:
tail -f /var/log/ufw.log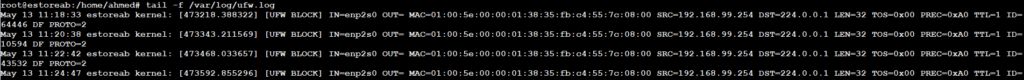
Filtering Logs:
You can filter UFW logs from other system logs using grep:
From syslog:
grep -i ufw /var/log/syslog
Or from kern.log:
grep -i ufw /var/log/kern.logLogging Levels:
or you can check live logs
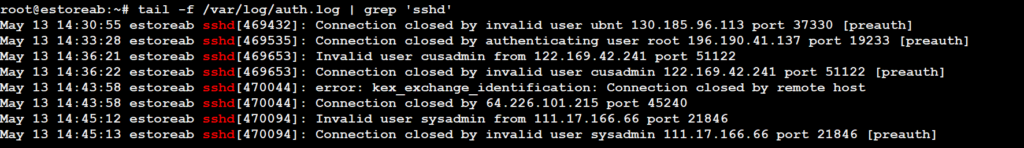
UFW supports different logging levels:
off: Logging disabled.
low: Logs blocked packets not matching current rules and logged rule entries.
medium: Includes invalid packets, new connections, and rate-limiting logs.
high: Adds rate-limiting logs.
full: Similar to high level but excludes rate limiting.
Best Practices and Tips
Regularly Review Rules:
Periodically assess your firewall rules to ensure they align with your security requirements.
Remove any unnecessary or outdated rules.
Limit Exposure:
Only allow necessary services and ports. Avoid leaving unused ports open.
Consider using application-specific profiles (e.g., for web servers, databases) to simplify rule management.
Rate Limiting:
Implement rate limiting rules to prevent abuse or brute-force attacks.
For example, limit SSH connections to prevent excessive login attempts:
sudo ufw limit OpenSSH
Prioritize Rules:
Rules are evaluated in order. Place more specific rules before general ones.
Deny rules should come before allow rules.
Logging and Monitoring:
Enable logging (as discussed earlier) to track firewall activity.
Regularly review logs for anomalies or unexpected behavior.
Backup Rules:
Save your UFW rules to a file for easy restoration:
sudo ufw export backup-rules.txtTest Changes Safely:
When modifying rules, test them first without applying them permanently:
sudo ufw --dry-run allow 8080
learn About Services:
Understand the services running on your system and their default ports.
Refer to /etc/services for a list of common service names and associated ports.
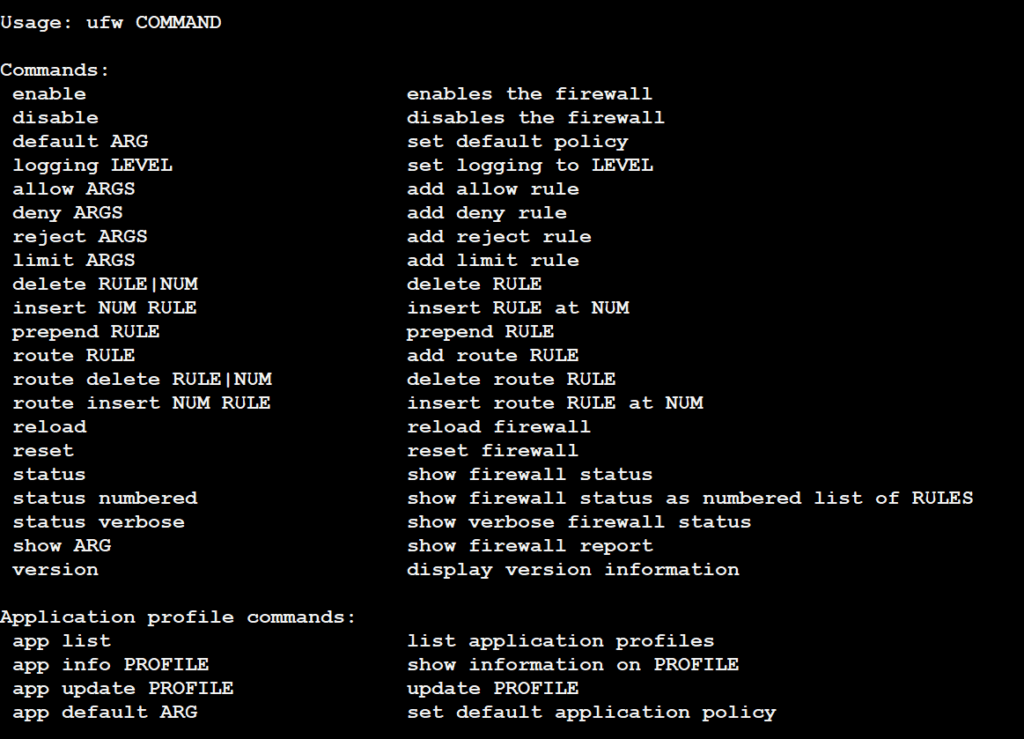
List of all commandes
- ufw enable: Enables the UFW firewall.
- ufw disable: Disables the UFW firewall.
- ufw status: Shows the current status of UFW, including enabled/disabled status and active rules.
- ufw status verbose: Provides a detailed status of UFW, including rules with interfaces and ports.
- ufw reload: Reloads the UFW firewall rules without disrupting existing connections.
- ufw reset: Resets UFW to default settings, removing all rules.
- ufw default [allow | deny | reject] [incoming | outgoing]: Sets default policies for incoming/outgoing traffic.
- ufw allow [port/service]: Allows traffic on a specific port or service.
- ufw deny [port/service]: Denies traffic on a specific port or service.
- ufw reject [port/service]: Rejects traffic on a specific port or service.
- ufw limit [port/service]: Limits the rate of incoming connections to a specific port or service.
- ufw delete [rule]: Deletes a specific rule from the UFW configuration.
- ufw insert [number] [rule]: Inserts a rule at a specific position in the rule list.
- ufw logging [on | off | [level]]: Enables or disables logging and sets the logging level.
- ufw app list: Lists available application profiles that can be used with UFW.
- ufw app info [profile]: Provides information about a specific application profile.
- ufw app update [profile]: Updates application profiles to reflect changes in installed applications.
- ufw app default [profile]: Sets the default application profile for UFW.
- ufw route allow [subnet]: Allows traffic from a specific subnet to pass through the firewall.
- ufw route delete [subnet]: Deletes a route added by
ufw route allow.





Pingback: The Ultimate Guide to Successful Advertising with AdCreative.ai
Pingback: becoming an Ubuntu expert
Pingback: 7 Essential Training Courses for Aspiring Web and Mobile Developers - EstoreAB
Pingback: Web and Mobile Developers
Pingback: High-Potential Cryptocurrencies for 2024
Pingback: The 10 Best Essential Mobile Apps You Can't Live Without - EstoreAB