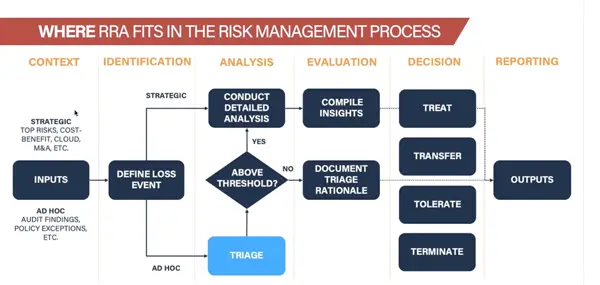
Rapid Risk Assessment
These questions are designed to support rapid threat modeling to identify risks in your plan. If you need any assistance, please contact the cybersecurity team.
A Rapid Risk Assessment apply on a user story or an architecture diagram.
Code Security Practices
What defensive coding practices are we following to protect against common vulnerabilities (e.g., SQL injection, XSS, CSRF)?
Are there any known vulnerabilities in the technologies or frameworks we are using for this project?
Authentication and Authorization
How are we handling user authentication and authorization?
Are there any potential weaknesses in these mechanisms?
Are we using multi-factor authentication (MFA) for critical access points?
Data Protection and User Privacy
How are we encrypting sensitive data, both at rest and in transit?
How are we generating and securing encryption keys?
Are there any privacy risks that could impact our users?
Dependency Security and Third-Party Risks
Are we incorporating well-maintained and secure third-party libraries and dependencies?
How do we manage and mitigate risks associated with open-source components?
Are there any regulatory or compliance requirements we need to meet, such as the General Data Protection Regulation (GDPR)?
Stakeholders for Security
Are there any constraints that could impact our ability to secure the project?
Are all stakeholders aware of the cybersecurity risks and their potential impacts on the project?
Incident Response and Security Monitoring
What is our plan for responding to a security incident related to this project?
What is our plan for ongoing security monitoring and threat detection once the project is live?
How do we ensure that security patches and updates are applied promptly?
Impact of Security Breaches
What are the potential business impacts of a security breach in this project?
How do we plan to mitigate the reputational and operational risks of a security incident?




