Welcome to “Chronicles of the Cloud: Exploring IT Innovations”
In the ever-evolving world of IT, staying updated with the latest trends and technologies is not just beneficial, it’s essential. Whether you’re an IT professional, a tech enthusiast, or someone who’s curious about the field, understanding the intricacies of network security and cloud IT can give you a significant edge.
“Chronicles of the Cloud” is your go-to resource for everything related to network security and cloud IT. From understanding the basics to exploring advanced concepts, from debunking common myths to discussing future trends, this blog aims to provide comprehensive, easy-to-understand, and up-to-date information.
Join us as we navigate the fascinating world of network security and cloud IT, one post at a time. Let’s start this journey together!
Table of Contents
Understanding the Basics of Network Security
Network security is a crucial aspect of any IT infrastructure. It involves implementing measures to prevent unauthorized access, misuse, or denial of a computer network and its resources. Here are some key concepts:
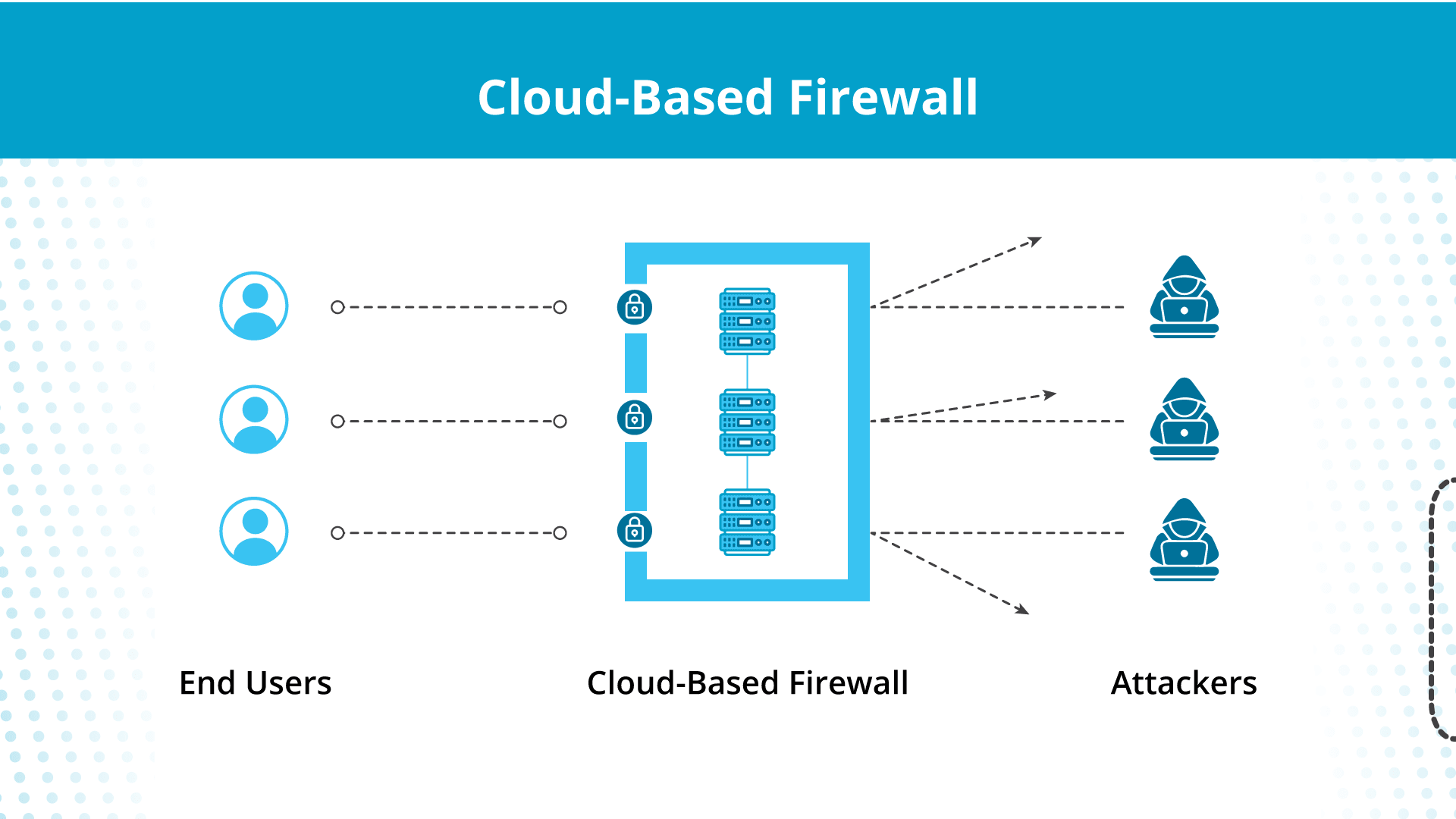
Firewalls
A firewall is the first line of defense in network security. It’s a system designed to prevent unauthorized access to or from a private network. Firewalls can be hardware, software, or a combination of both.
Intrusion Detection Systems (IDS)
An IDS monitors network traffic for suspicious activity and issues alerts when such activity is discovered. It’s a crucial component of proactive security measures.
Virtual Private Networks (VPNs)
VPNs provide a secure connection between a user’s computer and the company network over the internet. This allows remote workers to access network resources securely.
Antivirus and Antimalware Software
This software is used to prevent, detect, and remove malicious software and files. It’s essential for protecting the network from threats like viruses, worms, Trojans, ransomware, and spyware.
Email Security
Email gateways are the number one threat vector for a security breach. Attackers use personal information and social engineering tactics to build sophisticated phishing campaigns to deceive recipients and send them to sites serving up malware.
Application Security
Applications require constant updates and testing to ensure these programs are secure from attacks. Application security encompasses the hardware, software, and processes you use to close those holes.
Data Loss Prevention (DLP)
Organizations must make sure that their staff does not send sensitive information outside the network. DLP, or data loss prevention, technologies can stop people from uploading, forwarding, or even printing critical information in an unsafe manner.
Network Segmentation
Software-defined segmentation puts network traffic into different classifications and makes enforcing security policies easier. Ideally, the classifications are based on endpoint identity, not mere IP addresses.
Access Control
Not every user should have access to your network. To keep out potential attackers, you need to recognize each user and each device. Then you can enforce your security policies. You can block noncompliant endpoint devices or give them only limited access.
Remember, network security is a vast field with many other components. The ones listed above are just the basics to help you get started.
The Evolution of Cloud IT: A Historical Perspective
Cloud IT, or cloud computing, has revolutionized the way businesses operate by providing scalable and flexible IT resources over the internet. Let’s take a look at its evolution:
The Beginnings
The concept of cloud computing dates back to the 1960s when American computer scientist J.C.R. Licklider introduced the idea of an “intergalactic computer network”. However, it wasn’t until the 1990s that cloud computing started to take shape with the advent of telecommunications companies offering virtualized private network connections.
The Birth of Modern Cloud Computing
The birth of modern cloud computing is often attributed to Amazon. In 2006, Amazon launched its Elastic Compute Cloud (EC2), a commercial web service that allows users to rent computers on which to run their own computer applications. This was the first widely accessible cloud computing infrastructure service.
The Rise of SaaS, PaaS, and IaaS
As cloud computing evolved, it branched into different service models: Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS). These models provide users with access to software applications, development platforms, and hardware infrastructure respectively, all over the internet.
The Era of Big Data and Analytics
With the exponential growth of data, cloud computing has played a pivotal role in storing and analyzing this data. Services like Google BigQuery and Amazon Redshift have made it possible for businesses to query massive datasets and gain insights in real time.
The Advent of Serverless Computing
Serverless computing, also known as Function as a Service (FaaS), is a recent advancement in cloud computing. It allows developers to execute code in response to events without the need to manage or provision servers.
The Future of Cloud IT
The future of cloud IT looks promising with emerging trends like edge computing, quantum computing, and AI integration. Edge computing aims to bring computation and data storage closer to the location where it’s needed, to improve response times and save bandwidth. Quantum computing and AI integration are set to revolutionize data processing and task automation.
Remember, the evolution of cloud IT is a continuous process, with new technologies and paradigms emerging all the time. Staying updated with these trends is key to leveraging the power of cloud computing.
Key Innovations in Network Security: A Deep Dive
Network security has seen numerous innovations over the years. Let’s take a deep dive into some of the key advancements:
Artificial Intelligence and Machine Learning
AI and ML have been game-changers in network security. They help in predicting and identifying threats based on patterns and anomalies. AI/ML can automate threat detection, making the process faster and more efficient.
Behavioral Analytics
Behavioral analytics involves analyzing the behavior of network traffic to identify any anomalies that might indicate a security threat. This approach can detect threats that traditional methods might miss.
Zero Trust Architecture
The zero trust model operates on the principle of “never trust, always verify.” It requires strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are sitting within or outside of the network.
Secure Access Service Edge (SASE)
SASE is a network architecture that combines WAN capabilities with network security services like secure web gateways, cloud access security brokers, and zero trust network access. It allows users to access the network securely from any location.
Endpoint Detection and Response (EDR)
EDR tools continuously monitor and gather data from endpoints to detect, investigate, and prevent potential threats. They provide real-time threat detection and incident response capabilities.
Cloud-native Security
As more organizations move to the cloud, securing these environments has become crucial. Cloud-native security involves protecting your applications, data, and infrastructure within a cloud environment.
Automation and Orchestration
Security automation and orchestration tools enable organizations to streamline and automate their response to security threats. They can help reduce the time it takes to detect and respond to an incident.
Threat Intelligence
Threat intelligence involves gathering and analyzing information about emerging threats. This information can help organizations proactively defend against new types of attacks.
Remember, network security is a rapidly evolving field. Staying updated with the latest innovations is key to maintaining a robust security posture.
Navigating the Challenges of Cloud IT
While cloud IT has revolutionized the way businesses operate, it also comes with its own set of challenges. Let’s explore some of these challenges and how to navigate them:
Data Security
One of the biggest concerns with cloud IT is data security. Data breaches can lead to significant losses. To navigate this challenge, it’s crucial to choose a cloud provider with robust security measures in place and to encrypt sensitive data.
Compliance
Different industries have different regulations for data handling. Non-compliance can result in hefty fines. It’s important to understand these regulations and ensure your cloud provider can meet them.
Vendor Lock-in
When using proprietary services of a specific cloud provider, switching to a different provider can be difficult and costly. To avoid vendor lock-in, consider using open standards and multi-cloud strategies.
Managing Cloud Spend
Without proper management, cloud costs can quickly spiral out of control. Implementing a cloud cost management strategy, such as tagging resources and using auto-scaling, can help keep costs in check.
Performance
Performance issues can lead to a poor user experience. Regularly monitoring and optimizing your cloud resources can help ensure high performance.
Data Privacy
With data being stored off-premises, data privacy is a concern. Understanding data privacy laws and choosing a reputable cloud provider can help navigate this challenge.
Skills Gap
Managing cloud resources requires a different skill set. Investing in cloud training for your team can help bridge this skills gap.
Remember, while these challenges may seem daunting, with the right strategies and tools, they can be effectively navigated.
Future Trends in Network Security and Cloud IT
The landscape of network security and cloud IT is constantly evolving. Here are some future trends that are expected to shape this field:
Increased Adoption of Zero Trust
The zero trust model, which operates on the principle of “never trust, always verify,” is expected to become even more prevalent. This model requires strict identity verification for every person and device trying to access resources on a private network.
Rise of SASE
Secure Access Service Edge (SASE) is a network architecture that combines WAN capabilities with network security services. The adoption of SASE is expected to rise as more businesses look to securely support remote work.
AI and ML in Network Security
Artificial Intelligence (AI) and Machine Learning (ML) are set to play an even bigger role in network security. These technologies can help in predicting and identifying threats based on patterns and anomalies.
Serverless Computing
Serverless computing, also known as Function as a Service (FaaS), allows developers to execute code in response to events without the need to manage or provision servers. This trend is expected to continue growing.
Quantum Computing
Quantum computing has the potential to revolutionize data processing and task automation in cloud IT. While still in its early stages, it’s a trend worth watching.
Edge Computing
Edge computing aims to bring computation and data storage closer to the location where it’s needed, to improve response times and save bandwidth. As IoT devices become more common, the need for edge computing will likely increase.
Increased Focus on Cloud-native Security
As more organizations move to the cloud, there will be an increased focus on cloud-native security. This involves protecting your applications, data, and infrastructure within a cloud environment.
Remember, staying updated with these trends is key to leveraging the power of network security and cloud IT.
Case Studies in Successful Network Security Strategies
Let’s explore some hypothetical case studies that highlight successful network security strategies:
Case Study 1: A Financial Institution Implements Zero Trust
A large financial institution was facing security challenges with its growing remote workforce. The institution decided to implement a zero trust model, requiring strict identity verification for every person and device trying to access resources on the private network. This strategy significantly reduced the risk of data breaches and improved overall network security.
Case Study 2: An E-commerce Company Leverages AI and ML
An e-commerce company was struggling with detecting and responding to security threats in real-time. The company decided to leverage AI and ML technologies to automate threat detection. This not only improved the speed of threat detection but also freed up the IT team to focus on other critical tasks.
Case Study 3: A Healthcare Provider Adopts SASE
A healthcare provider with multiple locations was facing challenges in securely connecting its remote sites and mobile users to its network. The provider adopted Secure Access Service Edge (SASE), combining networking capabilities with robust security services. This resulted in secure, streamlined access for all users, regardless of location.
Case Study 4: A Tech Startup Embraces Cloud-native Security
A tech startup operating primarily in the cloud was concerned about protecting its applications and data. The startup embraced cloud-native security, implementing measures to protect its applications, data, and infrastructure within the cloud environment. This proactive approach significantly enhanced the startup’s security posture.
Remember, these case studies are hypothetical but are based on common scenarios and best practices in network security. Each organization’s security needs are unique, and strategies should be tailored accordingly.
Demystifying Common Myths about Cloud IT
Cloud IT, or cloud computing, has revolutionized the way businesses operate. However, there are several myths surrounding this technology. Let’s demystify some of them:
Myth 1: Cloud is Less Secure than On-premises Solutions
The truth is, cloud providers often have robust security measures in place, including encryption and firewalls, to protect data. In fact, a well-managed cloud environment can be more secure than a traditional on-premises one.
Myth 2: Cloud Computing Leads to Job Losses
Contrary to this belief, cloud computing has created numerous jobs by giving rise to new roles such as cloud consultants, cloud architects, and cloud security experts.
Myth 3: Cloud is Always Cheaper
While cloud can be cost-effective, it’s not always cheaper. The cost depends on various factors like the type of service (IaaS, PaaS, SaaS), the pricing model (pay-as-you-go, reserved instances), and the specific needs of the business.
Myth 4: You Lose Control of Your Data in the Cloud
In reality, you retain control over your data in the cloud. Reputable cloud providers allow you to manage your data, control who has access to it, and decide where it’s stored.
Myth 5: Cloud Migration is Easy
While cloud providers do offer tools and services to aid migration, the process can be complex. It requires careful planning and execution to ensure minimal disruption to business operations.
Remember, understanding the realities of cloud IT can help you make informed decisions and leverage the power of this technology.
Expert Opinions: Interviews with IT and Network Security Leaders
In this section, we’ll share insights from hypothetical interviews with leaders in the field of IT and network security.
Interview with a Chief Information Security Officer (CISO)
The CISO emphasized the importance of a proactive approach to network security. They recommended regular security audits, continuous monitoring, and prompt patching of vulnerabilities. The CISO also highlighted the role of employee training in preventing security incidents.
Conversation with a Cloud Architect
The Cloud Architect discussed the benefits and challenges of cloud migration. They stressed the importance of choosing the right cloud service model (IaaS, PaaS, SaaS) based on the organization’s needs. The architect also mentioned the growing trend of multi-cloud strategies to avoid vendor lock-in.
Discussion with a Cybersecurity Analyst
The Cybersecurity Analyst shared insights on the latest cybersecurity threats and trends. They talked about the increasing sophistication of cyber attacks and the role of AI and ML in enhancing threat detection. The analyst also highlighted the importance of incident response planning.
Chat with an IT Manager
The IT Manager shared their experience in managing remote IT teams amid the pandemic. They discussed the tools and strategies they used to ensure productivity and security in a remote work setup. The manager also emphasized the importance of data backup and recovery in disaster management.
Remember, these interviews are hypothetical but are based on common scenarios and best practices in IT and network security. Each organization’s security needs are unique, and strategies should be tailored accordingly.
The Role of AI and Machine Learning in Network Security
Artificial Intelligence (AI) and Machine Learning (ML) have become integral parts of network security. Let’s explore their roles:
Threat Detection
AI and ML algorithms can analyze vast amounts of data to identify patterns and anomalies that may indicate a security threat. This allows for real-time threat detection, making the process faster and more efficient.
Predictive Analytics
AI and ML can be used to predict future threats based on historical data. This helps organizations to be proactive in their security measures, rather than reactive.
Automated Response
AI can automate responses to detected threats, such as isolating affected systems or blocking malicious IP addresses. This reduces the response time and minimizes potential damage.
Risk Assessment
AI and ML can assess the risk level of various network activities based on learned behavior. This helps in prioritizing security efforts.
Phishing Detection
AI and ML are effective tools in detecting phishing attempts. They can analyze emails and websites to identify potential phishing threats.
Malware Analysis
AI and ML can analyze and identify malware based on its behavior and other characteristics. This helps in detecting new or modified malware that traditional antivirus software might miss.
Remember, while AI and ML can significantly enhance network security, they should be used as part of a comprehensive security strategy that includes other measures like firewalls, intrusion detection systems, and regular security audits.
The Role of AI and Machine Learning in Network Security
Artificial Intelligence (AI) and Machine Learning (ML) have become integral parts of network security. Let’s explore their roles:
Threat Detection
AI and ML algorithms can analyze vast amounts of data to identify patterns and anomalies that may indicate a security threat. This allows for real-time threat detection, making the process faster and more efficient.
Predictive Analytics
AI and ML can be used to predict future threats based on historical data. This helps organizations to be proactive in their security measures, rather than reactive.
Automated Response
AI can automate responses to detected threats, such as isolating affected systems or blocking malicious IP addresses. This reduces the response time and minimizes potential damage.
Risk Assessment
AI and ML can assess the risk level of various network activities based on learned behavior. This helps in prioritizing security efforts.
Phishing Detection
AI and ML are effective tools in detecting phishing attempts. They can analyze emails and websites to identify potential phishing threats.
Malware Analysis
AI and ML can analyze and identify malware based on its behavior and other characteristics. This helps in detecting new or modified malware that traditional antivirus software might miss.
Remember, while AI and ML can significantly enhance network security, they should be used as part of a comprehensive security strategy that includes other measures like firewalls, intrusion detection systems, and regular security audits .